THE INFORMATION IN THIS ARTICLE APPLIES TO:
- EFT v7.3.3 - 7.4.13.15
- EFT v8.0 adds advanced properties to an AdvancedProperties.json file instead of the registry.
When you upgrade to EFT v8, the non-default settings that you have defined in the registry will be added to the Advanced Properties file during upgrade. (Default settings become part of the EFT configuration files.) For more on how to use advanced properties, and for a spreadsheet of the advanced properties, please refer to the "Advanced Properties" topic in the help for your version of EFT.
See also:
DISCUSSION
When EFT is configured to use SAML (Web SSO) Authentication, you can add the Advanced Properties below so that EFT will bypass the WTC login page and take the user directly to the WTC interface.
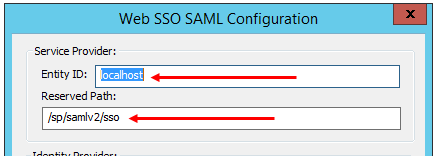
Also, ensure the IdP is directed to the EFT Reserved Path (e.g., , e.g., [hostaddress]/sp/samlv2/sso), which may be called the SSO URL in the IdP:
When the Identity Provider (IdP) sends an authentication request to EFT, it sends the SAML Response and the Assertion.
<SAML Response>
<Assertion>
</Assertion>
</SAML Response>
The IdP can sign the entire SAML Response or just the Assertion, or both, depending on the IdP. For that reason, we have two advanced properties to cover all cases. (This is useful if you have separate certificates for encryption and signing.)
To ignore or enforce the SAML assertion signature or SAML message signature, create the advanced properties below.
Prior to v8.0, add the advanced properties to the registry:
HKEY_LOCAL_MACHINE\SOFTWARE\Wow6432Node\GlobalSCAPE Inc.\EFT Server 7.4\
Type: DWORD
In v8.0 and later, add the advanced properties to the AdvancedProperties.JSON file.
{
"SamlAssertionSignatureEnforcementLevel":1,
"SamlMessageSignatureEnforcementLevel":0
}
Value name: SamlAssertionSignatureEnforcementLevel
Level of SAML assertion signature enforcement:
0 - required (default)
1 - not required if message signed
2 - enforce if present
3 - ignore result
4 - do not attempt verification.
Restart Required: yes
Backup/Restore: yes
----------------------------
Value name: SamlMessageSignatureEnforcementLevel
Level of SAML message signature enforcement:
0 - required
1 - enforce if present (default)
2 - ignore result
3 - do not attempt verification
Restart Required: yes
Backup/Restore: yes
For example:
- If the assertion is not signed, but the entire response is signed, then you could set SamlAssertionSignatureEnforcementLevel = to 1 (not required if response is signed) and SamlMessageSignatureEnforcementLevel = 0 (required)
- If the response is not signed, but the assertion is signed, then you could set SamlMessageSignatureEnforcementLevel = 2 (ignore result), and SamlAssertionSignatureEnforcementLevel = to 0 (required).
Refer to the help content and the following articles for information about configuring EFT and the IdP: