THE INFORMATION IN THIS ARTICLE APPLIES TO:
NOTE: This article provides guidelines for using a third-party tool with EFT. This article is not meant as formal support for that tool, but only as an example of setup options. Contact the third-party seller's support for detailed information about their product. Globalscape is not responsible for any configuration errors involving the third-party tool.
Overview
- This document outlines the steps needed to install and configure Shibboleth as the backend IDP server for use with testing EFT's SSO Feature.
- There are several ways to configure shibboleth for testing this covers one very basic installation that authenticates users against an LDAP server.
- Shibboleth backend that authenticates against an LDAP server
- Shibboleth and ADFS are the most ideal test IDPs for long term EFT Automation testing in that the other test servers (safenet, salesforce) are reside in the cloud outside of our control. Shibboleth however requires the most setup time.
Shibboleth Installation
- Download Shibboleth Identity provider for Windows.
- Follow the basic installation instructions and tests to verify successful install. If you get service unavailable or unauthorized add your IP address to the attribute-filter.xml file located at shibboleth\idp\conf
- https://wiki.shibboleth.net/confluence/display/IDP30/Installation
Starting and Stopping Shibboleth
- To restart the shibboleth service locate the shibd_idpw.exe application located at ..\shibboleth\idp\bin\ . The executable contains service restart buttons.
- After restarting the shibboleth service you will also need to restart the jetty web server application start.jar located at ..\shibboleth\jetty
You may want to make shortcut buttons to the aforementioned services since you will likely need to restart them often.
Shibboleth Configuration
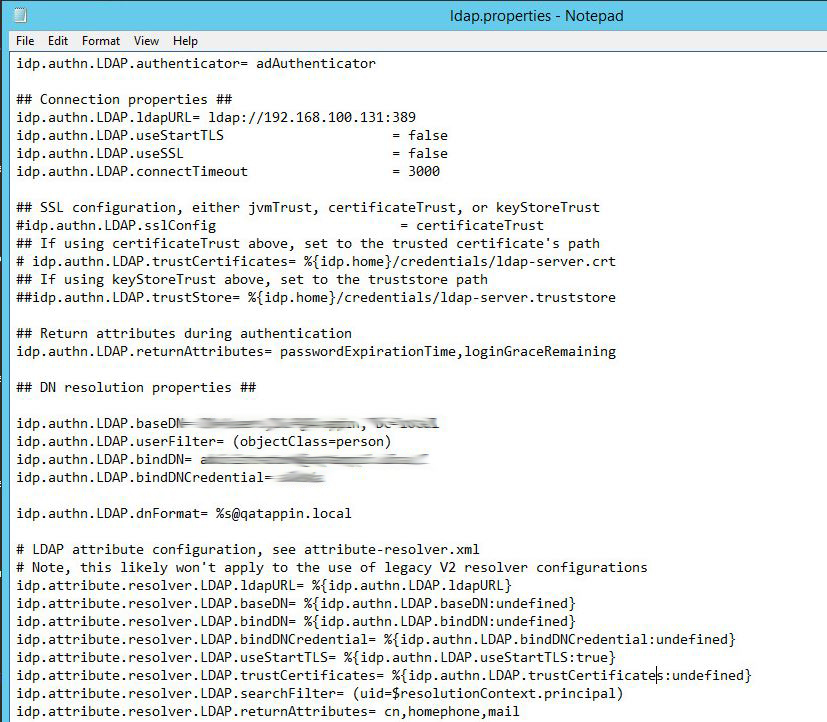
ldap.properties
Below is an excerpt of notable configuration items from the ldap.properties file located at ..\Shibboleth\idp\conf
- You will need to edit the ldap.properties file with your LDAP configuration that Shibboleth will be authenticating against.
- Open up the ldap.properties file located at ..\Shibboleth\IDP\conf
- Configure the connection properties.
- In the example below, SSL settings are set to false, if you choose to use SSL and set useSSL to true then you will need to obtain your LDAP server's certificate information and and the SSL settings below.
- Configure the DN Resolution Properties,
- Configure the Attribute Resolver properties.
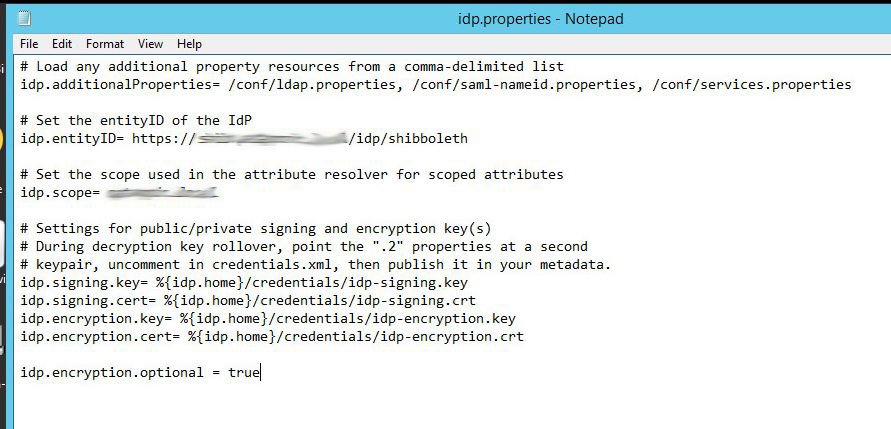
idp.properties
Below is an excerpt of notable configuration items from the idp.properties file located at ..\Shibboleth\idp\conf
- Take note of the idp.additionalProperites field, this field allows you to specify other properties files that will be imported into the shibboleth runtime.
- The idp.entityid can be found here, this value will be needed when configuring EFT's SSO Connection properties.
- Set the idp.scope equal to your domain.
- The location of the idp-signing.crt is also specified here. This certificate will need to be copied to your EFT System and specified in the SSO Configuration.
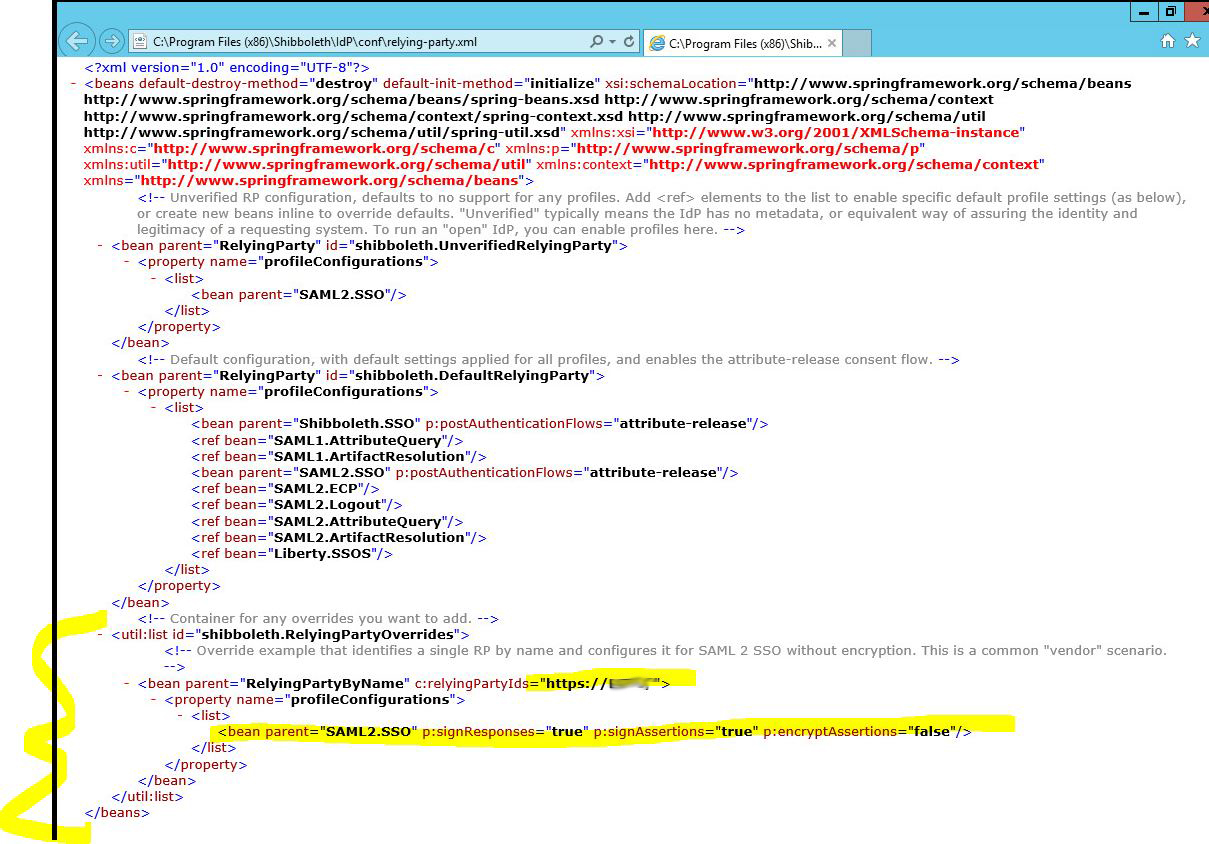
relying-party.xml
- For this example configuration, edit the rely-ing-party.xml file located in the config directory to signResponses, signEncryptions but to not encryptAssertions for communication with our EFT SP.
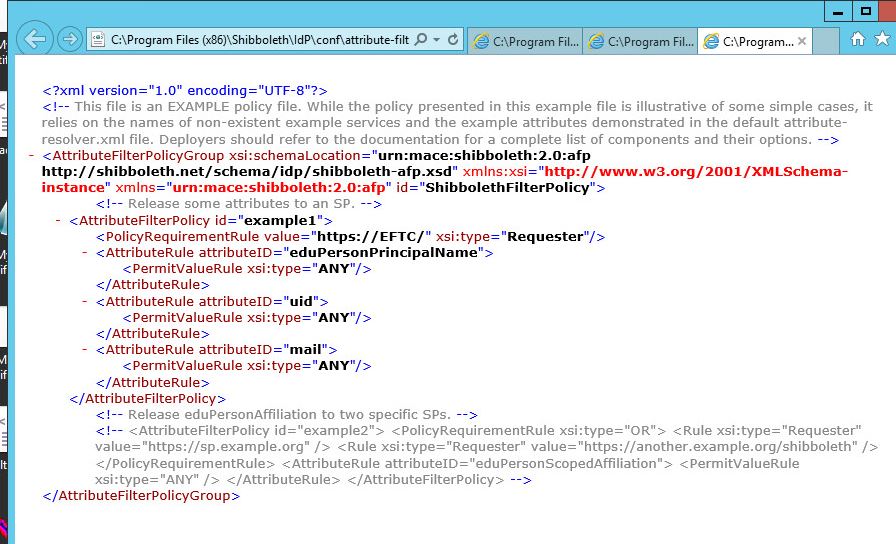
Mapping EFT Attributes to IDP > LDAP backend
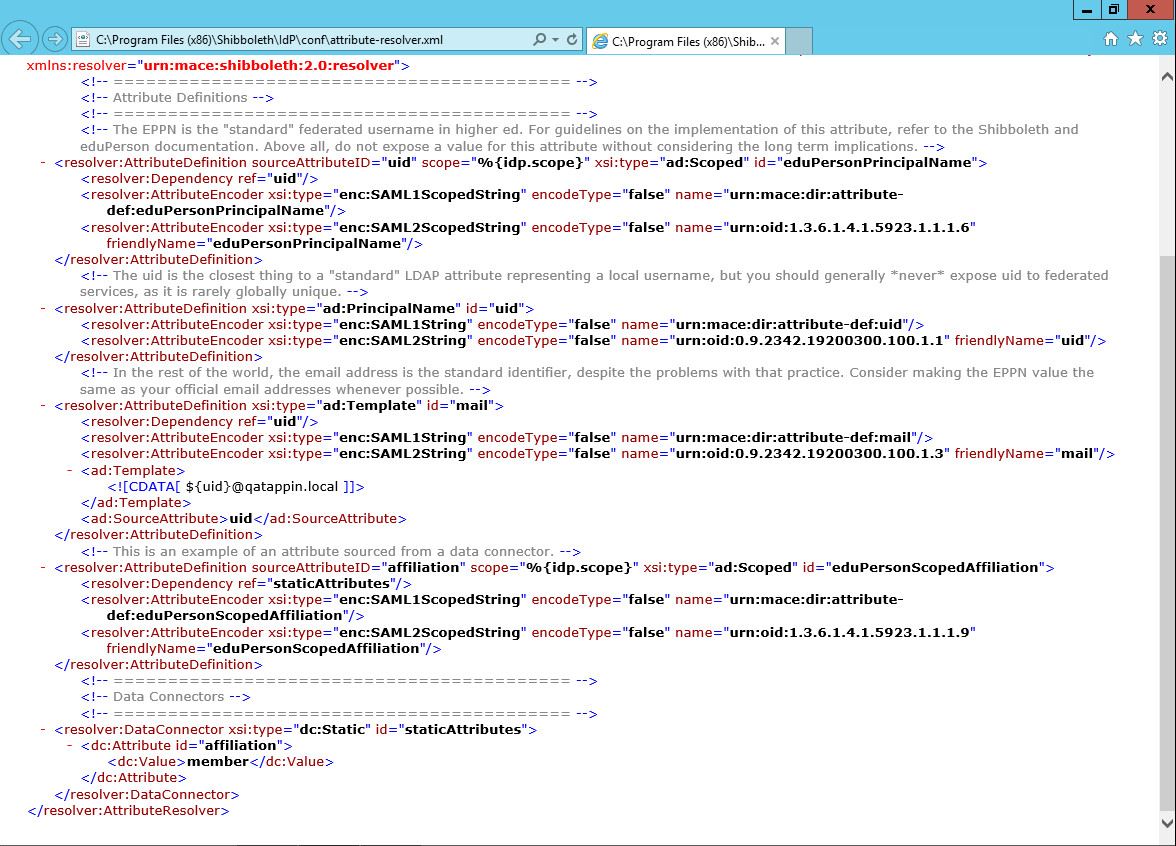
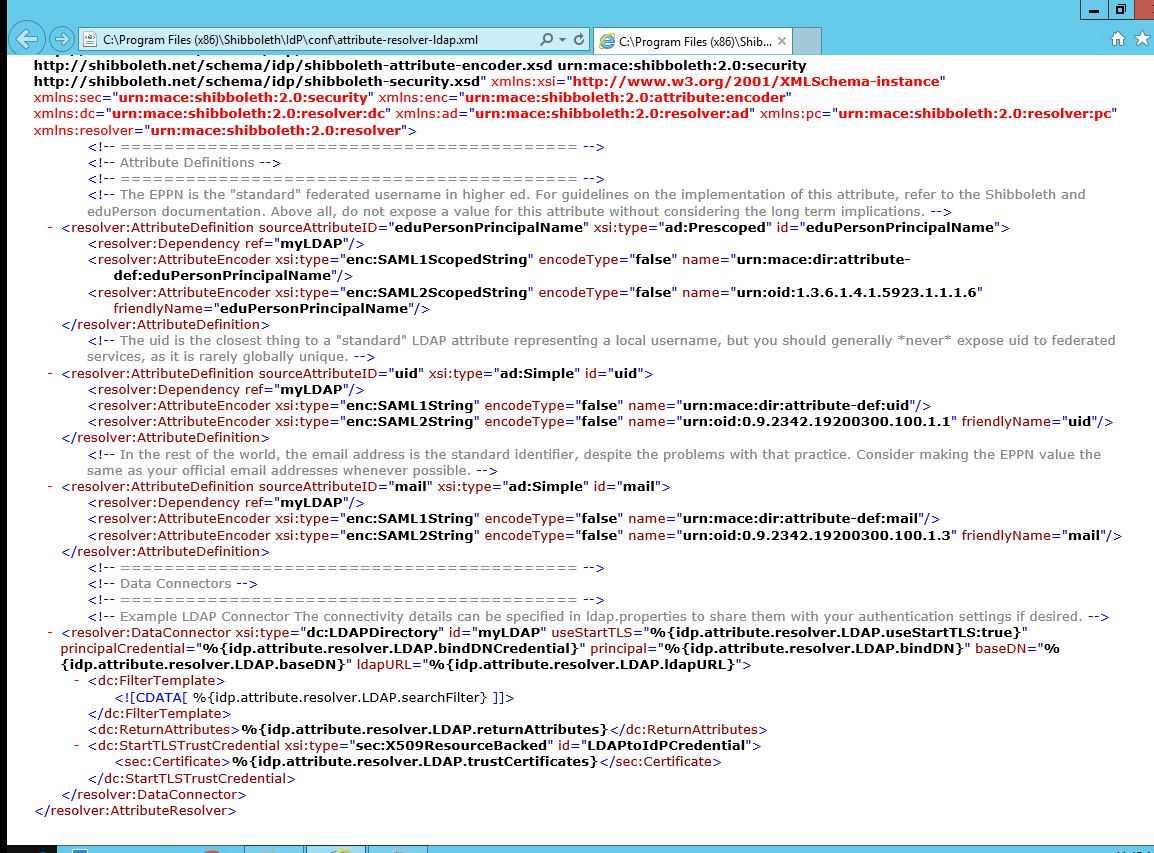
The attribute-filter, attribute-resolver and attribute-resolver-ldap files contain the attribute mapping/translations. In EFT we will supply a parameter attribute/nameid to the IDP. From there we need to define a mapping of the EFT attribute to the idp server to the ldap server.
Attibute-filter.xml
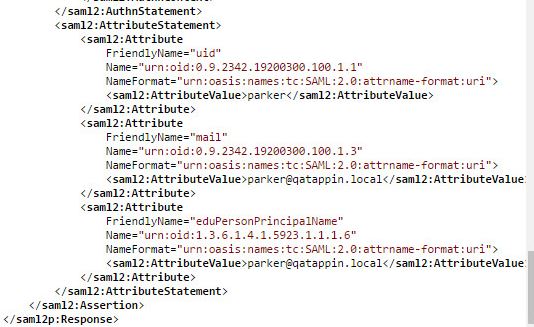
- This file determines which attributes we will return to the SP (EFT). Below if you sniff the SAML Response you will see the attributes defined in the attribute-filter.xml document.
- Below Image capture of a SAML Response to an EFT SP request:
Attribute-resolver.xml
Attribute-resolver-ldap.xml
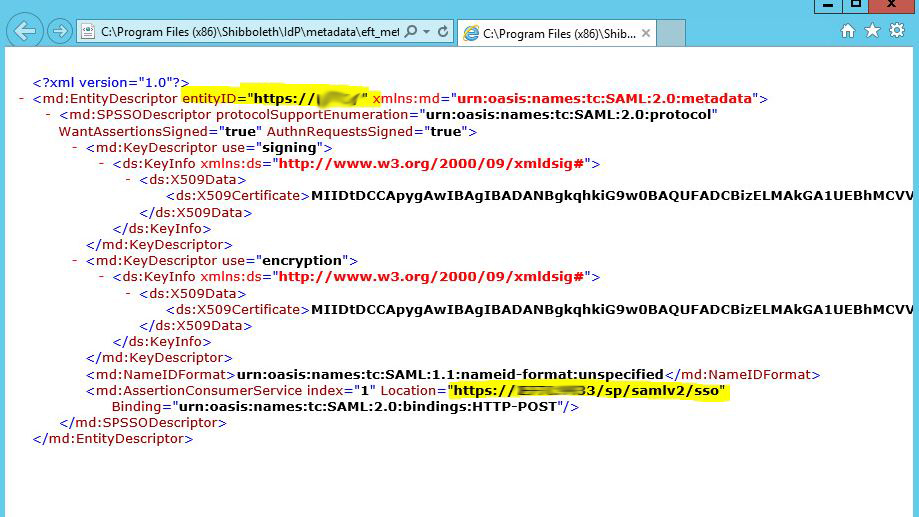
Specifying the EFT SP Metadata
EFT Metadata.xml File
- Pay special attention to the entityID value.
- When specifying the entity location property be sure to include the port number if EFT is listening on any port other than the default 443.
- For this example IDP configuration set the properties WantAssertionsSigned and AuthRequestsSigned = true.
- Place this file in the shibboleth\idp\metadata directory.
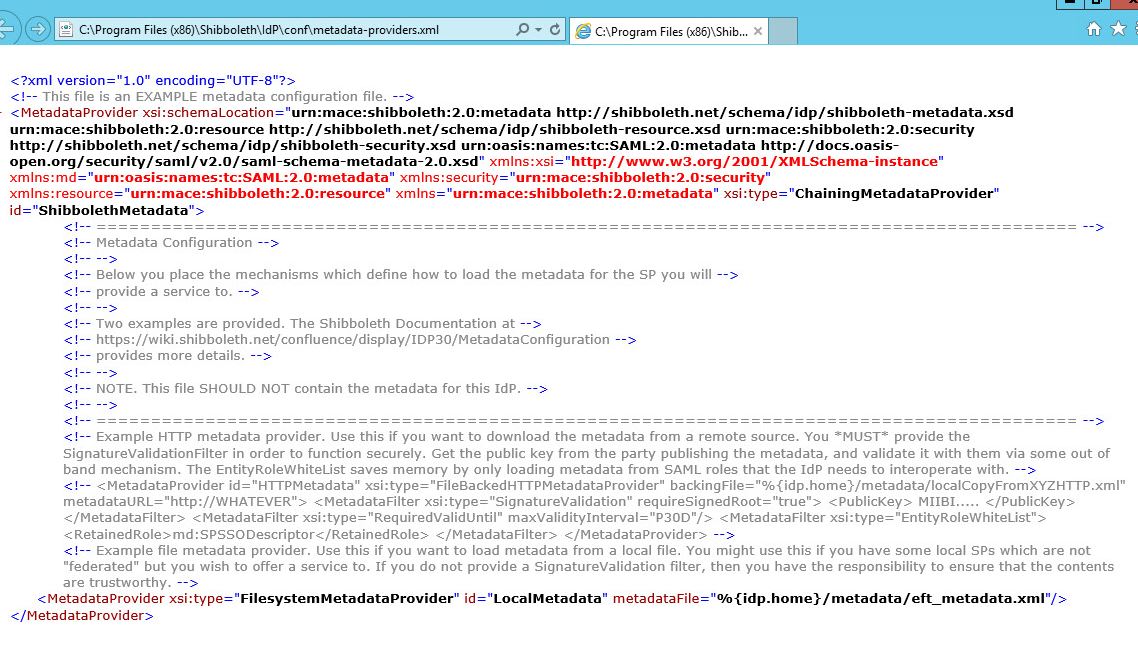
metadata-providers.xml
The metatdata-providers.xml file will need to be modified to show the location of the EFT Metadata file. The EFT_Metadata.xml file referenced in the example below is created and placed in the ...shibboleth\metatdata file location. The EFT_metadata file is how we communicate that EFT is an authorized Service Provider that will be using the Shibboleth IDP.
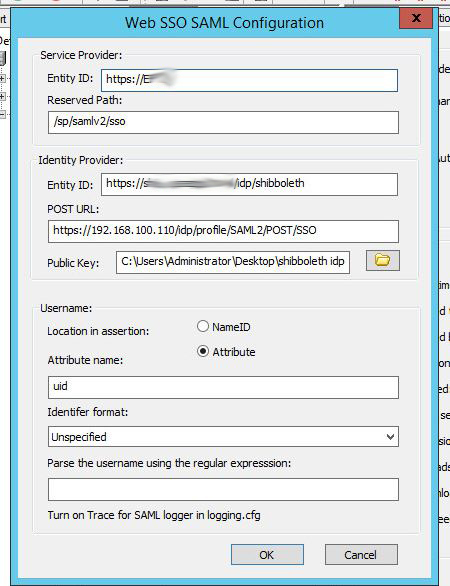
EFT Configuration
- The EFT site can just be a GS auth site with user names that exist on the LdAP backend.
- Configure EFT as follows, the idp properties can be found in the idp.properties as specified above.
- For the public key, copy the idp-signing.crt file from your shibboleth server to your EFT system and reference it in the SSO Settings. The idp-signing.crt file is automatically generated upon installation of the Shibboleth IDP server. It is located in the c:\program files(x86)\Shibboleth\idp\credentials folder.
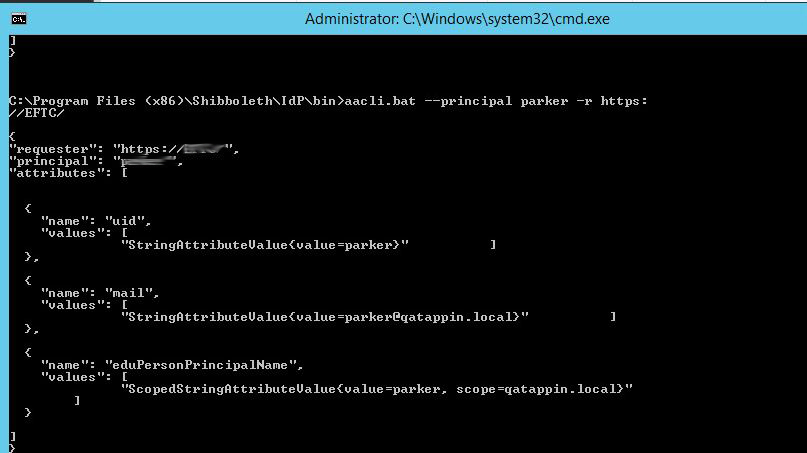
Test configuration of release attributes
- Shibboleth has a tool called aacli.bat where you can test if you configured your release attributes correctly. If you do not get the expected results then you need to examine your attribute-filter and attribute-resolver files.
Shibboleth Logging
- To up the logging level can be changed in the logback.xml file located in the ..\shibboleth\idp\conf directory.
- Logs are located in the ..\shibboleth\idp\logs directory.