THE INFORMATION IN THIS ARTICLE APPLIES TO:
- EFT v7.4.5.6 and later, running in non-clustered mode
DISCUSSION
On March 10th 2019, Globalscape released important security updates for our EFT™ Express and EFT™ Enterprise. These updates addressed recently identified potential security vulnerabilities that can affect system availability. They do not indicate data security risk. While there have been no reports of exploitation of production systems, we recommend upgrading as soon as possible to avoid potential risk.
Details
Vulnerability 1
- Area affected: Availability
- CVSS Score: 5.9 (medium)
- Vector string: CVSS:3.0/AV:N/AC:H/PR:N/UI:N/S:U/C:N/I:N/A:H/E:P/RL:O/RC:C
- Version affected: 7.4.5 and later, non-clustered only.
This vulnerability consists of a Denial-of-Service (DoS) vulnerability that, if exploited, would affect service availability. The vulnerability can be triggered by remotely accessing a non-publicized end-point (URL) on non-clustered EFT servers, resulting in a service crash. This end point has been present for some time with zero reported incidents; however, the specific end point is scheduled to be publicized as a Common Vulnerabilities and Exposures (CVE) event within the next 90 days (~late May, 2019). As such, we encourage our customers to patch their EFT within their next maintenance window, or within 90 days, whichever of the two dates comes first.
Vulnerability 2
- Area affected: Integrity
- CVSS Score: 3.7 (low)
- Vector string: CVSS:3.0/AV:N/AC:H/PR:N/UI:N/S:U/C:N/I:L/A:N/E:P/RL:O/RC:C
- Version affected: 7.4.5 and later
In this vulnerability, if a remote client provides an IP address via an X-Forwarded-For (XFF) header, rather than auditing the connection-derived IP, EFT will audit the XFF IP address to its ARM database, thus affecting the integrity of audited data. All other auditing, logging, and operational logic uses the client IP address derived from the connection itself. We addressed the issue by enforcing the general behavior of only auditing the connection-derived IP, ignoring any XFF provided value. For cases where customers are behind a load balancer or a proxy and want to leverage (and thus trust) the XFF header, we have provided an advanced properties override (described here: https://kb.globalscape.com/KnowledgebaseArticle11463.aspx).
DoS Vulnerability Q&A
Q. What is the risk of being exploited?
A. For an exploit to occur: First, it requires knowledge of the vulnerable end-point. Next, it requires the attacker to identify a vulnerable, non-clustered EFT server, which is challenging as EFT does not disclose its version nor its clustered state. Lastly, it requires that the attacker have the specific goal of affecting availability of a specific company, with their IP being logged at all stages of the attack. Based on this information customers may draw their own conclusion as to the risk involved.
Q. Why is the exact endpoint URL being made public?
A. This disclosure of the URL is outside of Globalscape’s control. The third-party security research firm that discovered the vulnerability has concluded that making the URL public would actually help affected customers validate that the patch was applied successfully and help vendors build WAF and IDS/IPS signatures to detect/block the attack.
Q. I’m running a patched version of EFT. How do I know if I’m affected?
A. If you are running a patched version based off of one the affected versions below you will need a cumulative patch. Further instructions are provided below. You may also contact your account representative or support for further assistance.
Q. Does the service crash affect data integrity or confidentiality, in addition to availability?
A. Confidentiality is not affected. If a service outage occurs, ongoing transfers will be interrupted; however, EFT supports the ability to manually and automatically resume interrupted transfers, depending on the remote client application capabilities. If there are event rules in progress, a service interruption could affect those, which may introduce risk to data integrity.
Q. Is there a workaround?
A. There are options to fix the vulnerability (see below) but no known workaround other than to block the affected endpoint upstream from EFT; however, affected customers would need to contact us for specifics as the URL will not be made public until after the CVE has been published (~ late May, 2019).
Versions Affected
The EFT Enterprise and Express versions list below are affected.
Note: The DoS vulnerability is not present in HA clustered installations.
Note: The DoS vulnerability is not present in EFT Arcus deployments.
- 7.4.13.14 (Enterprise and Express)
- 7.4.11.34 (Enterprise and Express)
- 7.4.10.6 (Enterprise and Express)
- 7.4.9.11 (Enterprise and Express)
- 7.4.7.18 (Enterprise and Express)
- 7.4.7.15 (Enterprise and Express)
- 7.4.5.8 (Enterprise and Express)
- 7.4.5.7 (Enterprise and Express)
- 7.4.5.6 (Enterprise and Express)
Next Steps
If you are an EFT Arcus customer or you are running EFT in an High Availability cluster then you are not affected by the DoS vulnerability and can refrain from updating unless you require the fix for the XFF bug.
The following options are available:
Option 1: Upgrade to the latest version, 7.4.13.15 (release 2): https://www.globalscape.com/products/eft-enterprise/support#7.4.13. This release contains the latest OpenSSH and OpenSSL libraries, enhanced HSTS header logic, and most importantly, addresses the DoS and XFF bugs. Upgrading to the latest version requires running the EFT installer and selecting “upgrade” when prompted. Of course, we recommend proper backup procedures prior to upgrading.
Option 2: For a less invasive fix, we offer a “patch” for each of the affected versions. The patch does not require a full install. Instead, you would simply download the appropriate patch, then replace the EFT service executable with the patched version. You can obtain patches for the affected versions from the download prior versions page here.See "Patching EFT" below for instructions for applying the patch.
Option 3: If you are currently running a patched version (or think you might be), you will need to determine which patch you are currently running, then contact your support representative [LINK] to request a cumulative patch that combines your current patches and the DoS/XFF patch.
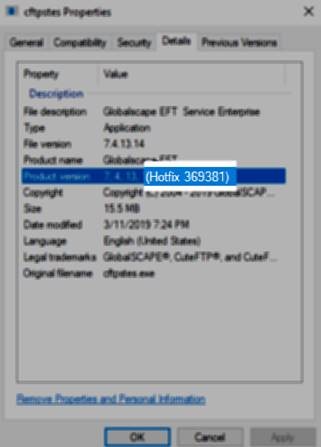
To determine your current patch version:
- Right click on the cftpses.exe file and select “Properties”
- Click the Details tab
- Look at the Product Version field.
- If you see Hotfix in that field, record that value prior to contacting us.
Patching EFT
After you obtain the correct patch (see link in Option 2) for your EFT version, perform the following steps to patch EFT:
- Close the EFT Administration UI (user interface) if open
- Stop the EFT Server Service
- Navigate to your EFT install path (default path c:\Program Files (x86)\Globalscape\EFT Server Enterprise\ or ...\EFT Server if express)
- Rename cftpstes.exe to cftpstes.exe_OLD
- Copy the hotfix to this directory
- Rename the hotfix to cftpstes.exe
- Start the EFT Server service
- Launch the administrator UI
To verify that the you have patched EFT correctly:
- Right click on the cftpses.exe file and select Properties.
- Click the Details tab.
- Look at the Product Version field.
- Look for the correct hotfix number following the product version.
"Hotfix 369381" is shown below. Your product version might be different from the one shown below.
In Closing
As always, Globalscape believes it is important to address security challenges and help our customers maintain their data’s confidentiality, integrity, and availability (CIA). It is this focus on security and our rigorous internal processes relating to vulnerability escalation that enabled us to quickly address the reported issue, implement a comprehensive remediation plan, and notify our customers of an available fix. Notwithstanding the foregoing, the information and content provided in this publication are not a guarantee or warranty and are provided on an "as is" basis. Please do not hesitate to contact us with any questions or suggestions on how to serve you, our customer, better.