THE INFORMATION IN THIS ARTICLE APPLIES TO:
- EFT versions prior to v8.1
SYMPTOM
AWE
tasks fail to execute when run via Event Rules when the EFT server service is running as a
domain account. Able to execute AWE tasks when running EFT server service as Local
System Account.
EFT.log
records the following error:
ERROR AWE <> - Error
creating AWE task
Code = 80070005
Code meaning = Access is denied.
Source = (null)
Description = (null)
The
Windows Event Log records the following entry to System events
Event
10016, DistributedCOM
The machine-default permission
settings do not grant Local Activation permission for the COM Server
application with CLSID {61282E0E-C031-4775-852C-3F8D9AD0730E} and
APPID Unavailable to the user <USERID> from address LocalHost
(Using LRPC) running in the application container Unavailable SID
(Unavailable). This security permission can be modified using the Component
Services administrative tool.
CAUSE
When
AWE executes tasks via Event Rules, the EFT server service launches the AWE
execution as a separate COM process under GSAWE.exe.
The
EFT server service requires appropriate folder, registry, and DCOM permissions
to execute properly.
RESOLUTION
Ensure that the EFT server service has the proper permissions as described below.
Folder Permissions:
- Provide
Full Control to the EFT program files. By default this is C:\Program Files (x86)\Globalscape. This can be located by opening Services.msc and checking the path to EFT server service executable:
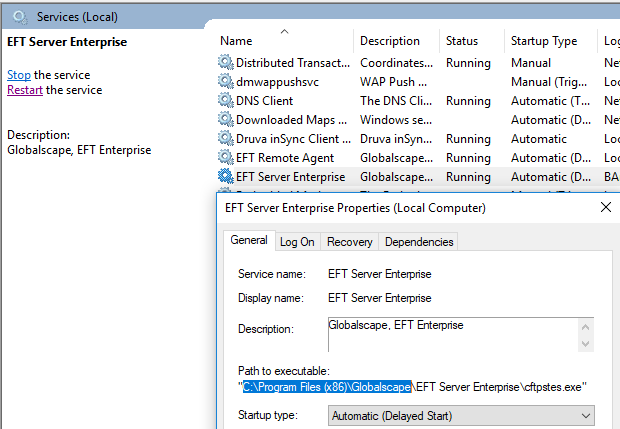
Ensure
that the EFT server service account has full control to the …\Globalscape\EFT Server Enterprise\AWE\bin folder.
Provide
Full Control to the C:\ProgramData\AutoMate folder
- Ensure
that EFT server service account has full control to the local and shared configuration
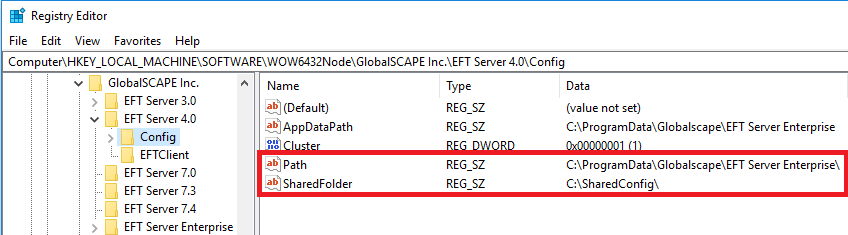
location (if running in HA). The configuration folder path can be found via the
registry:
HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\GlobalSCAPE
Inc.\EFT Server 4.0\Config
Path = Local configuration location
SharedFolder = Shared configuration location
(if running HA)
Registry
Permissions:
Open the registry editor (Start > Run > regedit.exe) and ensure that the EFT server service account has full control to the following locations:
HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\GlobalSCAPE Inc.
HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Globalscape
HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Network Automation
HKEY_CLASSES_ROOT\AppID\{AF778776-A08E-415A-A982-649B4DD69FAB}
HKEY_CLASSES_ROOT\AppID\GSAWE.EXE
HKEY_CLASSES_ROOT\WOW6432Node\AppID\{AF778776-A08E-415A-A982-649B4DD69FAB}
HKEY_CLASSES_ROOT\WOW6432Node\AppID\GSAWE.EXE
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\AppID\{AF778776-A08E-415A-A982-649B4DD69FAB}
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\AppID\GSAWE.EXE
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\AppID\{AF778776-A08E-415A-A982-649B4DD69FAB}
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\AppID\GSAWE.EXE
HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Classes\AppID\{AF778776-A08E-415A-A982-649B4DD69FAB}
HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Classes\AppID\GSAWE.EXE
HKEY_CLASSES_ROOT\GSAWE.GSAWETaskInterpreter
HKEY_CLASSES_ROOT\GSAWE.GSAWETaskInterpreter.1
HKEY_CLASSES_ROOT\WOW6432Node\CLSID\{61282E0E-C031-4775-852C-3F8D9AD0730E}
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\GSAWE.GSAWETaskInterpreter
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\GSAWE.GSAWETaskInterpreter.1
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{61282E0E-C031-4775-852C-3F8D9AD0730E}
HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Classes\CLSID\{61282E0E-C031-4775-852C-3F8D9AD0730E}
HKEY_CLASSES_ROOT\TypeLib\{DE4F36F3-3234-46E0-8BFD-64E6D4A0B1F3}
HKEY_CLASSES_ROOT\WOW6432Node\TypeLib\{DE4F36F3-3234-46E0-8BFD-64E6D4A0B1F3}
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\TypeLib\{DE4F36F3-3234-46E0-8BFD-64E6D4A0B1F3}
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\TypeLib\{DE4F36F3-3234-46E0-8BFD-64E6D4A0B1F3}
HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Classes\TypeLib\{DE4F36F3-3234-46E0-8BFD-64E6D4A0B1F3}
HKEY_CLASSES_ROOT\WOW6432Node\CLSID\{280301C3-5A4A-4F59-ACBD-CDE07B02C2F6}
HKEY_CLASSES_ROOT\WOW6432Node\Interface\{280301C3-5A4A-4F59-ACBD-CDE07B02C2F6}
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\CLSID\{280301C3-5A4A-4F59-ACBD-CDE07B02C2F6}
HKEY_LOCAL_MACHINE\SOFTWARE\Classes\WOW6432Node\Interface\{280301C3-5A4A-4F59-ACBD-CDE07B02C2F6}
HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Classes\CLSID\{280301C3-5A4A-4F59-ACBD-CDE07B02C2F6}
HKEY_LOCAL_MACHINE\SOFTWARE\WOW6432Node\Classes\Interface\{280301C3-5A4A-4F59-ACBD-CDE07B02C2F6}
DCOM Permissions:
- Open a Command prompt as administrator and run comexp.msc /32
- Open Component Services > Computers > My Computer > DCOM Config.
- Right-click “GSAWE” and open properties. Navigate to Security and grant full permission to the EFT server service account for Launch and Activation, Access, and Configuration Permissions.
- Right-click on “GSAWETaskInterpreter Class" and open properties. Navigate to Security and grant full permission to the EFT server service account for Launch and Activation, Access, and Configuration Permissions.
Reinstall and re-register ddls
Re-installing the AWE application files may rule out the possibility of a corrupted installation or missing application files.
- Stop the EFT server service and rename the EFT Program Files (By default this is C:\Program Files (x86)\Globalscape), once again, check Services.msc to verify the EFT installation path.
- Run the EFT installer and select Repair install.
- This should recreate the Program Files along with the AWE binary files. As part of the repair install, the AWE .dlls will be re-registered.
- The AWE dlls can be manually re-registered without performing an installation by running the ReRegisterDLLS.bat file found in the EFT Program Files folder.
Anti-virus exception
- Ensure that your anti-virus excludes real-time scanning of the program files for EFT.