THE INFORMATION IN THIS ARTICLE APPLIES TO:
- EFT and EFT
Enterprise, all versions
DISCUSSION
The "ROBOT Vulnerability" (CVE-2017-13099) is a
serious vulnerability with SSL/TLS. "Bleichenbacher’s Oracle Threat" is an older
vulnerability that affected SSL encryption and has recently resurfaced to
affect TLS encryption. The vulnerability allows attackers to break the
confidentiality of TLS-based connections. What this means for data is that an
attacker can record traffic and will later be able to decrypt and view it in
plain text.
EFT
supports TLS connections for HTTPS and FTPS. The ROBOT vulnerability only
affects RSA encryption key exchange. EFT has the ability to independently
enable and disable the RSA key exchange so that it can be set across the
server. Because of the vulnerability at hand, it is highly recommended that
you verify that the RSA key exchange is disabled or disable it if it isn’t
already.
This does not affect RSA with regards to user authentication in EFT. The Workaround below is only disabling RSA as a form of key exchange, which will occur before the user authentication and won’t have any negative effects on RSA authentication in EFT.
WORKAROUND
- Log in to the EFT
administration interface, and click the Server tab.
- In the left pane,
click the server node.
- In the right pane, click the Security tab.
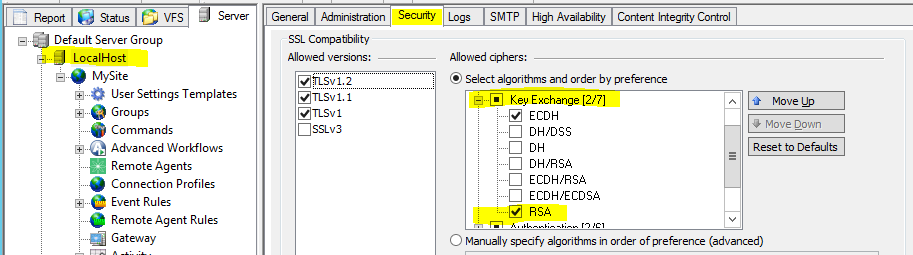
- Under SSL
Compatibility, Allowed ciphers, expand the Key Exchange node, and clear the check box to disable RSA, if selected.
- Choose Apply at
the bottom to save your changes.
- You will be prompted to restart all Sites. Click Yes to restart.
The
following screenshot shows the section described in the above steps with RSA unselected.
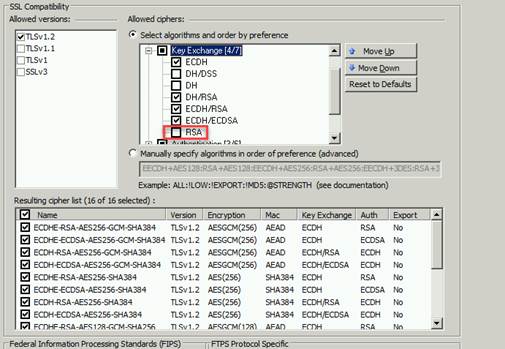
The bottom portion of the above screenshot shows a set of
ciphers that will pass when RSA is cleared, although yours may vary.