THE INFORMATION IN THIS ARTICLE APPLIES TO:
- EFT, 7.4.x and earlier
- EFT v8.x, TLS 1.2 is set by default
DISCUSSION
Q: What is GlobalSCAPE’s response to the SSL/TLS BEAST exploit?
A. GlobalSCAPE is aware of information that has been published describing a
new method to exploit a known vulnerability in SSL 3.0 and TLS 1.0. This
vulnerability affects the protocol itself and is not specific to EFT Server. We
are not aware of a way to exploit this vulnerability in other protocols or
components and we are not aware of attacks that try to use the reported
vulnerability at this time and do not consider this vulnerability a high risk
to GlobalSCAPE EFT Server customers.
Mitigating Factors:
The
attack must make several
hundred HTTPS requests before the
attack could be successful.
TLS 1.1, TLS 1.2, and all cipher suites that do not use CBC mode are not affected.
WORKAROUND
Re-prioritize the RC4 algorithm so that it is favored over CBC-based ciphers.
The attack only affects cipher suites that use symmetric encryption algorithms in CBC mode
(such as AES) and does not affect
the RC4 algorithm. You can prioritize the RC4 algorithm in EFT Server’s SSL settings in order to facilitate secure communication using RC4 instead of CBC-based ciphers.
- Log in to EFT Server as a Server Administrator.
- Click the Server node.
- Click the Security tab.
- Under Allowed ciphers, move RC4 128 bit to the top of the list.
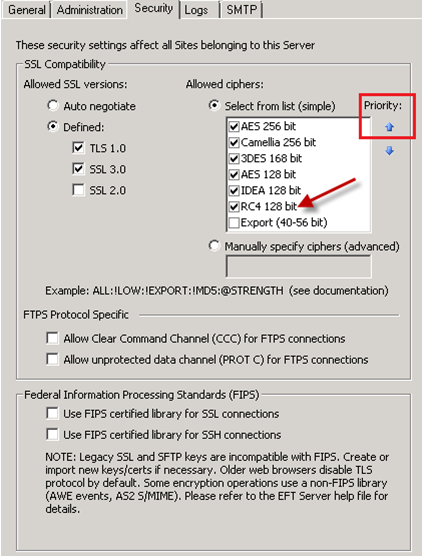
- Restart the EFT Server service.
Note: This Workaround refers to a setting or configuration change that does not correct the underlying issue but would help block known attack vectors until a security update is available. Future updates may include newer versions of the TLS protocol, change to default prioritization of ciphers, and/or additional controls in place to
eliminate all risk of an exploit.