THE INFORMATION IN THIS ARTICLE APPLIES TO:
- EFT, version 7 and later in a clustered or HA environment
QUESTION
Why do clients connect to EFT showing the IP of the Netscaler load balancer?
ANSWER
Security features in EFT, such as DoS prevention and banning IP addresses, depend on
being able to see the IP addresses from the clients that are connecting to EFT.
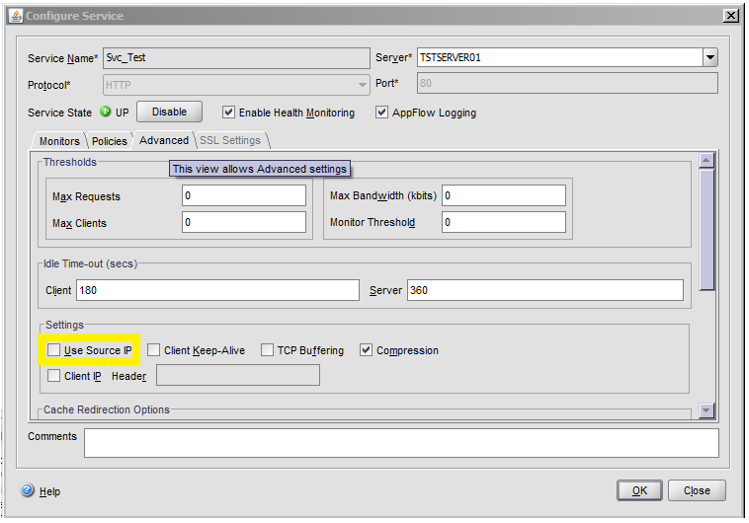
To use Source IP on configuring service
- On the DMZ Gateway servers being load-balanced, set the default gateway at the Windows OS TCP/IP settings to the SNIP IP (Netscaler’s Subnet IP – i.e. its interface on the local subnet) instead of the subnet’s default gateway IP.
- In on Netscaler’s Configure Service dialog box, select the Use source IP check box.
- Click OK to save your changes and dismiss the dialog box.
MORE INFORMATION
*Note: EFT shares the configuration between NODES, so whatever is on Node A is also on Node B, Node C, etc.
- bridging (pass through) the SSH key to either server
- bridging the SSL directly to the DMZ Gateways
However, it is possible to use “reverse proxy” or non-bridging:
- SSL terminates at the NLB using imported Signed SSL certificate.
- Either the traffic goes from https->http
- Or you terminate the SSL certificate on NLB and then re-secure the SSL between NLB and DMZ Gateway.