THE INFORMATION IN THIS ARTICLE APPLIES TO:
DISCUSSION
This article provides instructions for configuring EFT to use SAML authentication for end user access in this or similar scenario:
- User A logs in and has an account that is JIT provisioned.
- User A shares a workspace with user B, who has never logged in, but has a valid SAML account.
- User B receives a workspace notification but, instead of logging in with SSO credentials for access, is directed to go through the guest user registration process.
To configure SAML for JIT provisioning
- Be sure you are using EFT v8.0.4 or later.
- In the Web SSO SAML Configuration dialog box, select the Redirect to the SSO Service bypassing the standard login page check box.
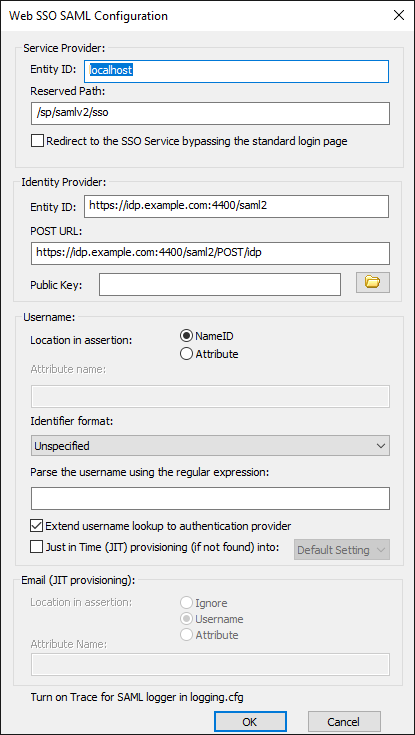
- Ensure that the advanced property “InviteeRegistrationRoute“ is set to “LoginPage”
- When the invitee follows the Workspaces invitation link, they will be routed to the login page, and then auto-redirected to the SSO IdP. The IdP authenticates the user, which will then be JIT provisioned in EFT.
The flow is as shown below:
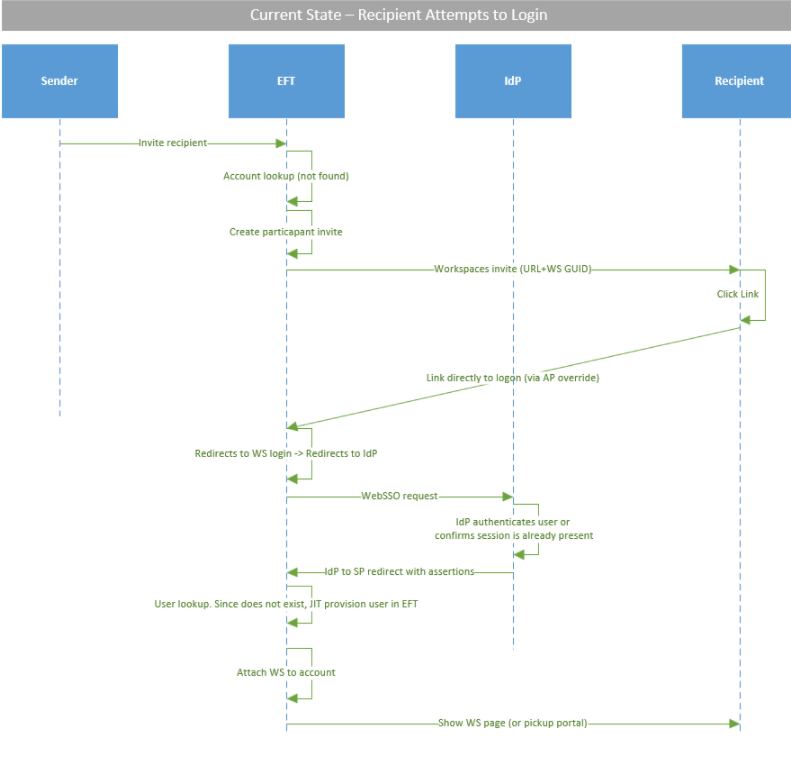
If you don’t want automatic routing to your IdP, then the user must click the SSO button on the login page before being redirected to the IdP login:
- Be sure you are using EFT v8.0.4 or later.
- In the Web SSO SAML Configuration dialog box, select the Redirect to the SSO Service bypassing the standard login page check box.
- Ensure that the advanced property “InviteeRegistrationRoute“ is set to “LoginPage”.
- When the invitee follows the Workspaces invitation link, they will be directed to the login page, on which they need to click SSO. The user is redirected to the SSO IdP, and the IdP authenticates the user, which will then be JIT provisioned in EFT.