THE INFORMATION IN THIS ARTICLE APPLIES TO:
See also:
Okta is an independent provider of identity for the enterprise, used by many organizations to provide Single Sign-On (SSO) capability across the enterprise. This article describes how to integrate the Okta dashboard with EFT Enterprise for SAML SSO.
To integrate OKTA with EFT Enterprise, you must:
- Enable the Advanced Security Module
- Ensure that SAML / Web SSO is enabled
- Ensure that you have enabled HTTPS
- Ensure that you have already created an SSL certificate
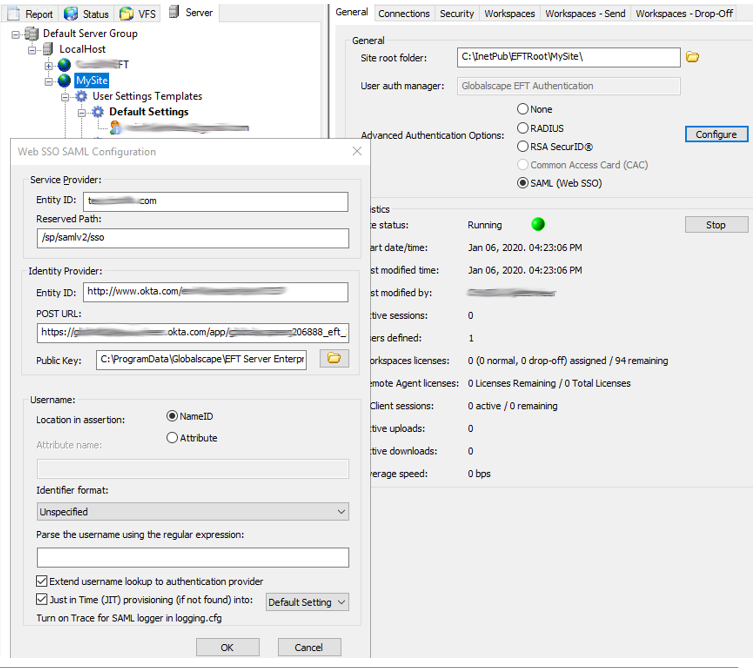
You will need the information from the Web SSO SAML Configuration dialog box in EFT:
- Service Provider Entity ID
- Reserved Path
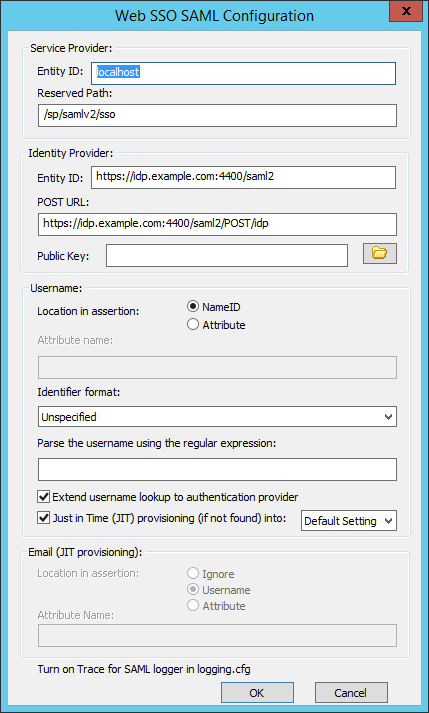
- Gather the Service Provider information from EFT
- Create the App
- Platform: Web
- Sign on Method: SAML 2.0
- Single sign on URL: https://entityid/reservedpath
- Audience URI: https://entityid
- Optional: Preview the SAML Assertion
- Assign users to the application (Assignments)
- Provide SAML 2.0 setup instructions to EFT
- Log in to your Okta account as a user with administrative privileges.
- Click Admin.
- Click Add Applications.
- Click Create New App.
- In the dialog that appears, click the “SAML 2.0” option, then click Create.
- In Step 1 General Settings, enter “Globalscape “ in the App name field, then click Next. (Optional: Add the EFT or Globalscape logo)
- In Step 2 Configure SAML section A SAML Settings, type the URL into the Single sign on URL and Audience URI (SP Entity ID) fields.
- In the Attribute Statements section, add three attribute statements:
- Set FirstName to user.firstName
- Set LastName to user.lastName
- Set Email to user.email
- Click Next to continue.
- In Step 3 Feedback, select I’m an Okta customer adding an internal app, and This is an internal app that we have created, then click Finish.
- The Sign On section of your newly created Example SAML Application application appears.
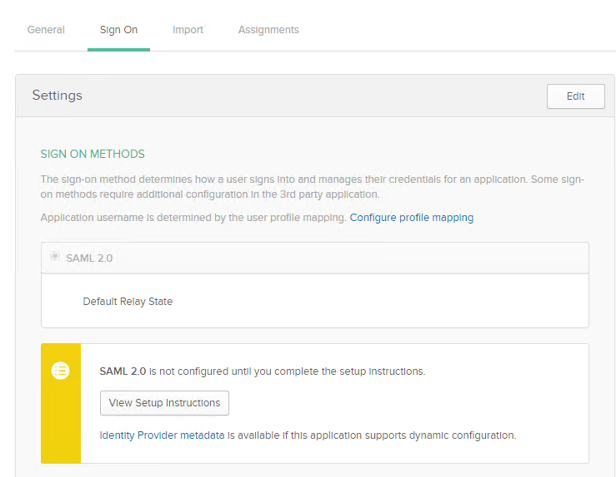
- Click View Setup instruction to complete the setup instructions.
- Click Identity Provider metadata and copy the download to your EFT \ProgramData\ directory. Make sure you save it as an XML file.
If all is correct, the Okta User can now click the "Globalscape App" and see the Globalscape WTC Login Page, with SSO Login enabled.
In EFT, enable trace logging in logging.config for the SAMLSSO logger:
01-02-20 16:55:43,302 [5996] DEBUG SAMLSSO <HTTP.ProcessRequest> - authnstatement count = 1
01-02-20 16:55:43,302 [5996] DEBUG SAMLSSO <HTTP.ProcessRequest> - notBefore 1578005536 notOnOrAfter 1578006136 (now is 1578005743)
01-02-20 16:55:43,302 [5996] DEBUG SAMLSSO <HTTP.ProcessRequest> - Assertion::Conditions Condition count 0
01-02-20 16:55:43,302 [5996] DEBUG SAMLSSO <HTTP.ProcessRequest> - Assertion::Conditions OneTimeUse count 0
01-02-20 16:55:43,302 [5996] DEBUG SAMLSSO <HTTP.ProcessRequest> - ProcessAssertion returns AssertionSuccess, numSuccessfulAuthnStatements = 1
01-02-20 16:55:43,302 [5996] DEBUG SAMLSSO <HTTP.ProcessRequest> - final check: Status code is 'urn:oasis:names:tc:SAML:2.0:status:Success', username is '********.com', numSuccessfulAuthnStatements = 1
01-02-20 16:55:43,333 [5996] DEBUG SAMLSSO <HTTP.ProcessRequest> - CHTTPSocket::HandleSAMLSSO - RelayState is '/'
01-02-20 16:55:43,333 [5996] DEBUG SAMLSSO <HTTP.ProcessRequest> - CHTTPSocket::HandleSAMLSSO - RelayState is '/' and SavedPathCookie is '/'. SavedPathCookie is more specific so that takes precedence.
01-02-20 16:55:43,333 [5996] TRACE SAMLSSO <HTTP.ProcessRequest> - CHTTPSocket::HandleSAMLSSO - looking for absolute prefix https://test.********.com/
01-02-20 16:55:43,349 [5996] DEBUG SAMLSSO <HTTP.ProcessRequest> - CHTTPSocket::HandleSAMLSSO - m_bEmbeddedDownloadLinkRequest = false for /
01-02-20 16:55:43,349 [5996] DEBUG SAMLSSO <HTTP.ProcessRequest> - CHTTPSocket::HandleSAMLSSO - EFT user was authenticated by IdP and successfully logged in
01-02-20 16:55:43,349 [5996] DEBUG SAMLSSO <HTTP.ProcessRequest> - CHTTPSocket::HandleSAMLSSO - redirecting to path /