THE INFORMATION IN THIS ARTICLE APPLIES TO:
DISCUSSION
This article describes how to enable Azure Active Directory Single Sign-on with EFT Arcus and the Web Transfer Client
Prerequisites
- Azure Active Directory (AAD) Premium
- EFT Arcus Site Administrator privileges
- A WTC user in EFT Arcus
- AAD user matching the WTC user in EFT Arcus
Create a new Azure AD SSO application
- Log into the Azure Portal with a Global Administrator account.
- Open Azure Active Directory (Figure1) and create a new Enterprise Application.
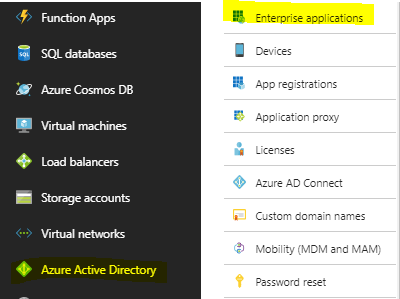
- Click Non-gallery application and give the application a display name.
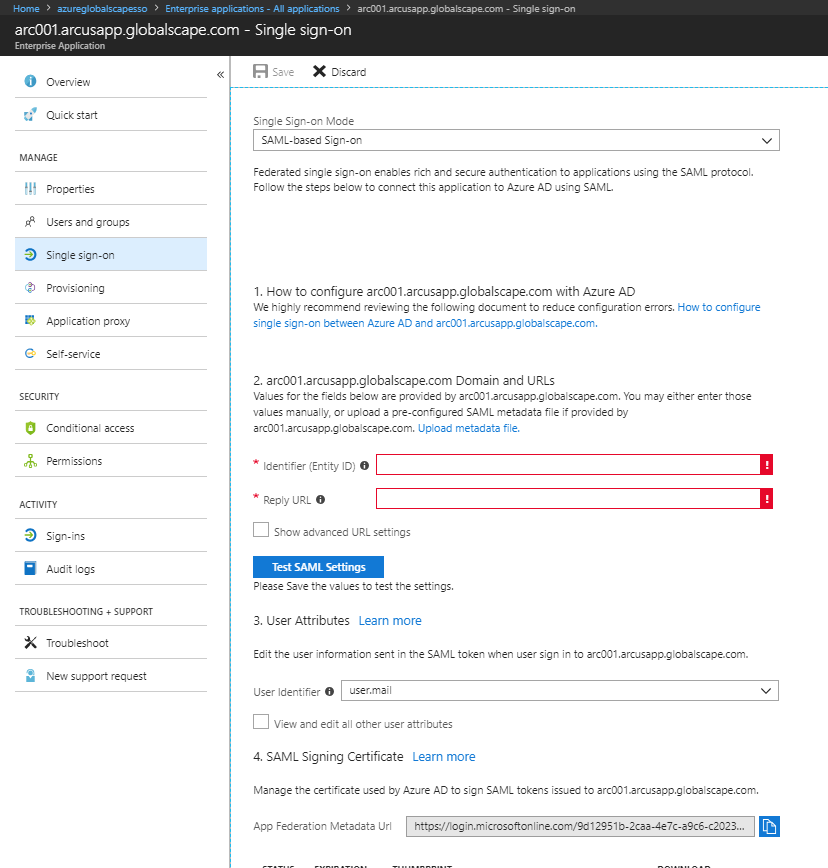
- Click SAML-based Sign-on on the drop-down list.
You should see a screen like Figure 2:
- Don’t forget to add users to your enterprise application in Azure AD!
Keep this browser open and log into EFT Arcus.
Enable SAML in EFT Arcus
- Select the EFT Arcus Site on which you will configure SAML.
- In the General box, under the Advanced Authentication Options, click SAML (webSSO).
- Click Configure.
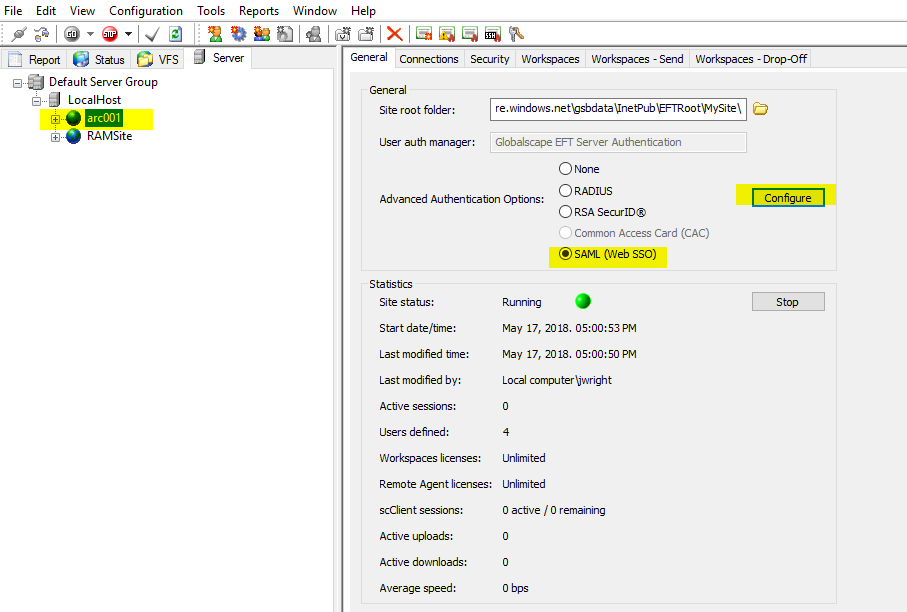
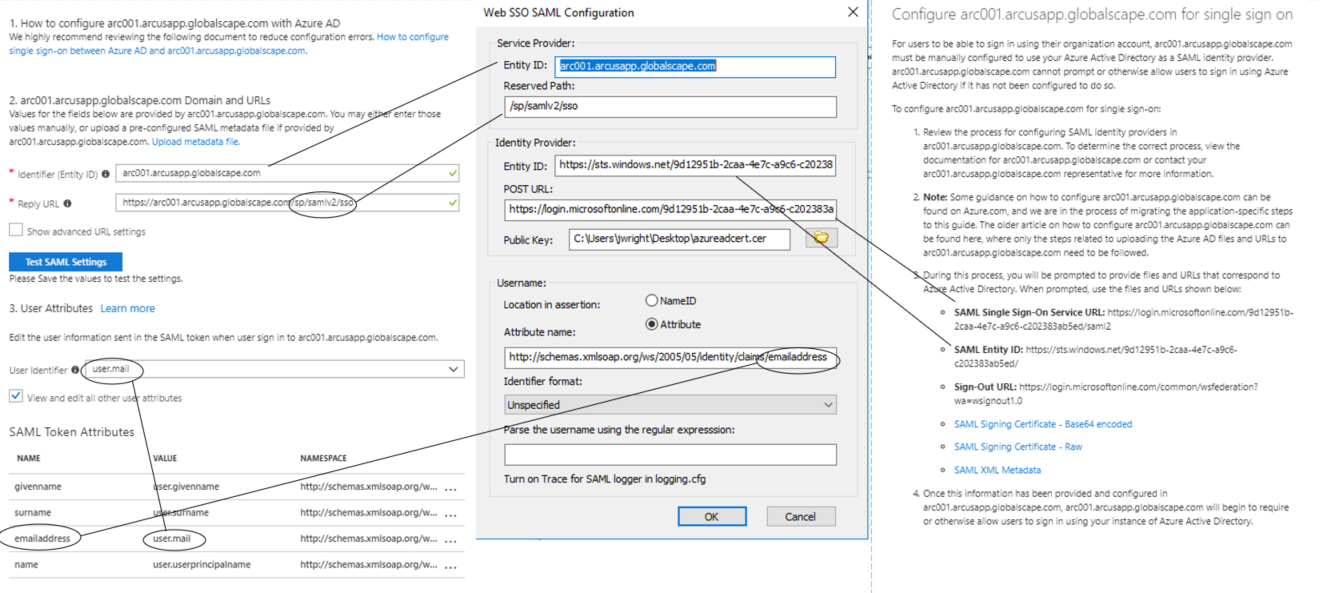
The Web SSO SAML configuration dialog box appears.
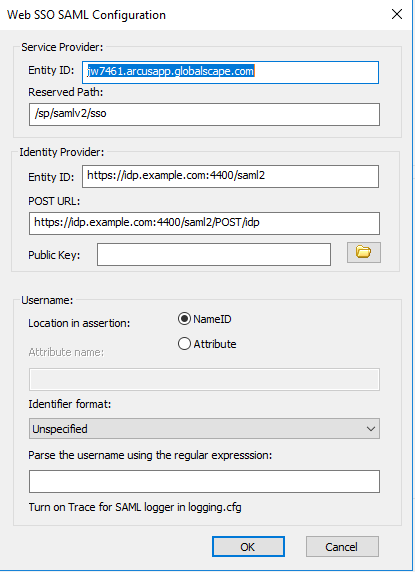
Configure SAML settings
At the end of these steps you can view an image of the value mapping.
- In the EFT Arcus Web SSO SAML Configuration dialog box, copy the EntityID value.
- Copy the value to Azure AD – Identifier (Entity ID).
- Copy the Reserved Path value to Azure AD – Reply URL.
- Prepend the value in the Reply URL text box with your unique domain and protocol. In this example, we were issued the domain arc001.arcusapp.globalscape.com. So, our reply URL would look like: https://arc001.arcusapp.globalscape.com/sp/samlv2/sso
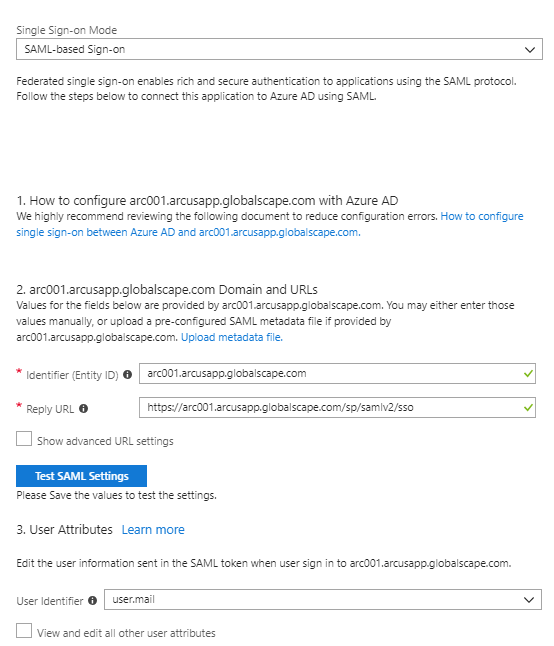
- In Azure AD, select the User Attributes you’d like to authenticate. In the example provided, we’re using an email address.
- Download the SAML Signing Certificate using the Certificate (RAW) link
- (Optional) – Configure an email address to be notified when the certificate is due to expire
- In Azure, click Configure.
- In Azure, copy the URL for SAML Single Sign-On Service URL
- In EFT Arcus, paste this value in the Identity Provider text area in the POST URL text box.
- In Azure, copy the URL for SAML Entity ID.
- In EFT Arcus, paste this value in the Identity Provider text area in the Entity ID text box.
- Upload the public key to EFT Arcus. (At the time of this writing, this can only be done by creating a support ticket as EFT Arcus customers only have Site Admin privileges.)
- In EFT Arcus, in the Identity Provider text area, fill in the path to the public certificate uploaded in the previous step.
- In EFT Arcus, under the username text area, click Attribute.
- In the Attribute text box, enter the attribute you’re expecting from Azure AD. We configured this setting in step 5.
- Note that Azure AD is using full schema URLs as their attribute names. In our example using an email address would look like this: http://schemas.xmlsoap.org/ws/2005/05/identity/claims/emailaddress
- Click OK and allow the EFT Arcus site to restart.
At this point, you should be able to navigate to your Web Transfer Client. Do not enter any credentials; click SSO sign on.
Don’t forget to add users to your enterprise application in Azure AD!