THE INFORMATION IN THIS ARTICLE APPLIES TO:
- EFT, v7 and later in HA mode
PROBLEM
Typically load balancers sit between clients are servers and are configured to NAT translation so internal IP addresses/ports are never revealed to the outside world and likewise external IP address/ports are never seen by a server. The F5 has what it calls SNATs (Smart NAT) which can be explicitly setup per network or made to work automatically. When it is in place the F5 will replace the IP address/port for every incoming packet with virtual ones.
Although this is generally a secure way of configuring a load balancer, one disadvantage to this setup is that the server behind the LB will only see the F5 IP address.
For EFT this can affect such areas as:
- ARM reports
- Logging
- IP Ban
- Event rules
- AWE tasks
Event rules will be limited, ARM reports will show transactions all coming from the same IP Address, and regular traffic will appear as a DOS attack.
SOLUTION
One way to deal with this is to allow client IP addresses to pass through to the servers behind the LB. It is relatively easy to have the F5 device setup for this. The biggest consideration in doing this is that each server in the pool must have their default gateway pointing to the F5 box (that is, unless the clients are internal and will be on the same subnet as the servers).
MORE INFORMATION
This assumes that you already have your F5 setup with nodes, a pool of either EFT or DMZ Gateway servers, and you are setting up your virtual server (i.e., to provide HTTPS service).
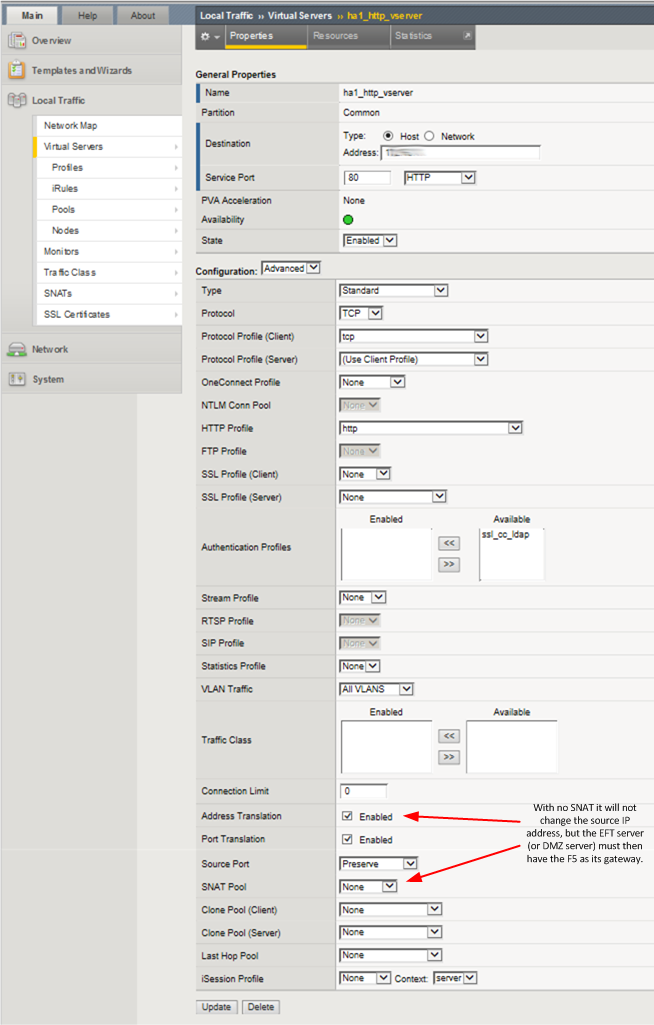
- Select the virtual server you want to configure.
- Make sure the Address Translation checkbox is checked and the SNAT is set to None.
- For every EFT server (or DMZ instead, if that is used) in the associated pool, you must set the F5 as the default gateway.
NOTES:
- This applies to non-HTTP protocols because the HTTP headers do this already.
- The load balancer/traffic manager and DMZ Gateway must be on the same VLAN.