THE INFORMATION IN THIS ARTICLE APPLIES TO:
- EFT Enterprise version 6.3 - 7.3.7.12
- For EFT Enterprise v7.4.2.4 and later, and 7.3.7.12 and later, see an additional registry requirement below.
(Required for all systems using Internet Explorer with Integrated Windows Authentication (IWA))
DISCUSSION
EFT Server allows for Single Sign-On (SSO) support for HTTP/S connections when Integrated Windows Authentication (IWA) is explicitly enabled. The change will apply to all Sites in EFT Server that use Active Directory authentication. Currently, Internet Explorer (IE) is the only browser that fully supports IWA. Users connecting with other browsers must still go through the normal login page.
Form-based login as implemented in the normal login page is generally considered superior for interactive user connections because it facilitates true session management. However, IWA is a legitimate alternative for use within internal corporate networks. With IWA enabled, EFT Server defers the user authentication to Active Directory and IE, resulting in a single sign-on user experience. Users whose credentials are accepted by AD are not prompted for a username and password, and are instead logged directly into the EFT Server client web interface without any further input.
The downside to IWA is that in skipping the normal login page, the user misses out on a few of the functions accessed from that page, such as providing alternate credentials or choosing whether to load the Web Transfer Client (WTC), though an administrator may still disable WTC access for an individual user or entire Settings Template if necessary. Additionally, the user must close their browser to end the session rather than using a logout button. In an environment where SSO is a requirement, these functions may not be important or even desired.
NOTE:
- When IWA is enabled, the SSO functionality only applies to AD sites for interactive users connecting with IE. No other scenario is affected.
- When navigating to the WTC, the fully qualified domain name of the EFT Server host must be used.
- EFT must be added as a trusted site in the browser.
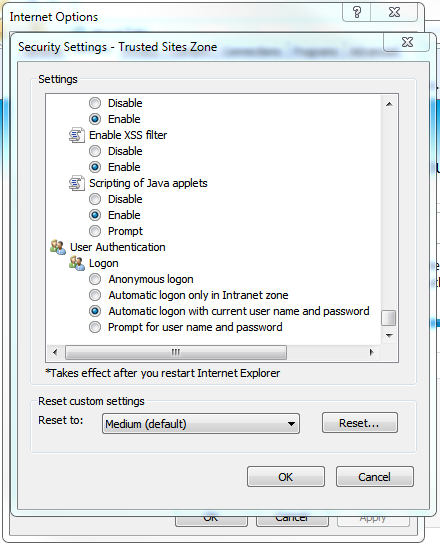
- User Authentication\Logon in the Security Settings dialog box for the Trusted Sites Zone must be set to Automatic logon with current user name and password. (By default Automatic logon only in Intranet zone is selected, but using this setting will cause Windows to prompt the user for their AD credentials before going on to the WTC.)
REGISTRY SETTINGS
Restart Internet Explorer after creating or changing these settings.
To enable IWA for SSO, the following registry entries must be created and set appropriately on the EFT computer:
32 bit:
HKLM/SOFTWARE/GlobalSCAPE Inc./EFT Server 4.0/EFTClient/
64 bit:
HKLM/SOFTWARE/Wow6432Node/GlobalSCAPE Inc./EFT Server 4.0/EFTClient/
DWORD:use_registry
Value: 1= enabled
32 bit:
HKLM/SOFTWARE/GlobalSCAPE Inc./EFT Server 4.0/EFTClient/
64 bit:
HKLM/SOFTWARE/Wow6432Node/GlobalSCAPE Inc./EFT Server 4.0/EFTClient/
DWORD: enable_iwa
Value: 1= enabled
ADDITIONAL REGISTRY FIX FOR EFT ENTERPRISE v7.3.7.12 & 7.4.2.4
Required for all systems using Internet Explorer with Integrated Windows Authentication (IWA)
Add the following registry value:
(EFT Enterprise v7.3.7.12 and later, and v7.4.2.4 and later are only supported on a 64-bit OS.)
HKEY_CURRENT_USER/Software/Microsoft/Windows/CurrentVersion/Internet Settings/
DWORD: DisableNTLMPreAuth
Value: 1 = enabled
ADDITIONAL RESOURCES
https://support.microsoft.com/en-us/help/251404/you-cannot-post-data-to-a-non-ntlm-authenticated-web-site
https://stackoverflow.com/a/41004109