THE INFORMATION IN THIS ARTICLE APPLIES TO:
QUESTION
How do I prevent users from uploading malicious files to EFT?
ANSWER
The EFT file transfer server allows you to connect with any industry-standard file-transfer client to transfer files. In theory, those files could have a virus, or include malware, or contain information that violates company policy. EFT implements several safeguards to prevent unwanted files. The first layer of defense is authentication and user access permissions, which allows you to permit or block standard file transfer operations (upload, download, rename, etc.). Additional safeguards include the ability to block files with specified extensions, detect whether a user has renamed an uploaded file (to circumvent the blocked file extension), integrate with content inspection/virus detection software, or rely on locally running anti-virus/malware detection software. The procedure below describes how you can configure an EFT Site to block file extensions, detect when a file is renamed, and scan the file with antivirus/DLP tools via an ICAP server. EFT auditing and reporting can also show you which user or IP address uploaded the file, in case you need to take steps such as disabling the user account or banning their IP.
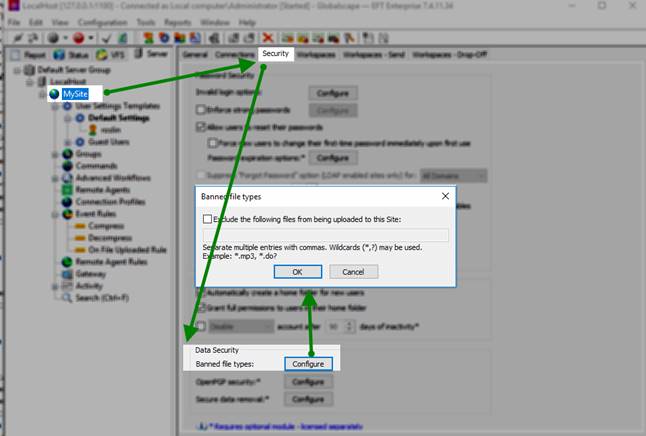
First, designate which extensions are allowed (not allowed) for uploads:
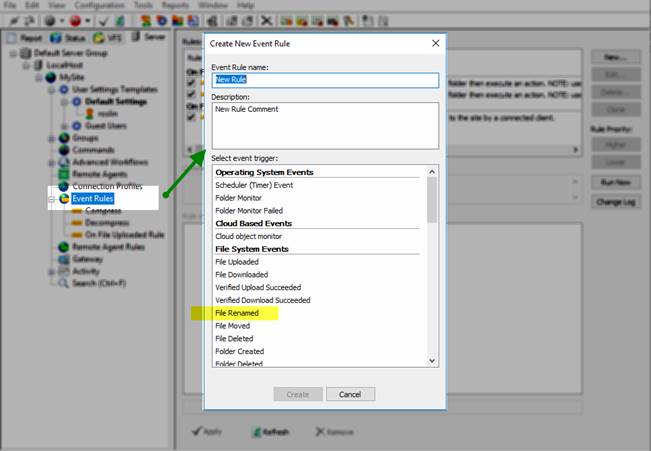
Create an Event Rule that detects, renames, and if a file is renamed to an EXE extension, perform an action (delete the file, send a notification, or other).
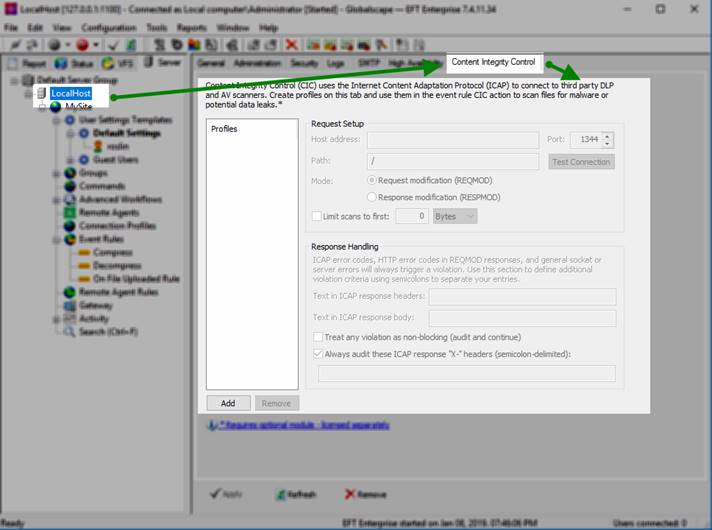
Of course, you should also consider setting up a virus scanner or similar file inspector, and leverage EFT’s ICAP protocol to integrate with that solution. The "Content Integrity Control" action allows EFT to identify and block malicious files, regardless of extension, or prevent the loss of company confidential information (if linked to a DLP device).